You Are Using an Insecure Hash Algorithm in CA Signature: How to Fix It! Secure hash algorithm (sha-1)
If you are looking for How To Fix NET:: ERR_CERT_WEAK_SIGNATURE_ALGORITHM you've came to the right place. We have 25 Pics about How To Fix NET:: ERR_CERT_WEAK_SIGNATURE_ALGORITHM like R8500 OpenVPN error you are using insecure hash al... - NETGEAR Communities, Openvpn You Are Using Insecure Hash Algorithm and also What is hash function? And how does it work | ssla.co.uk. Here it is:
How To Fix NET:: ERR_CERT_WEAK_SIGNATURE_ALGORITHM
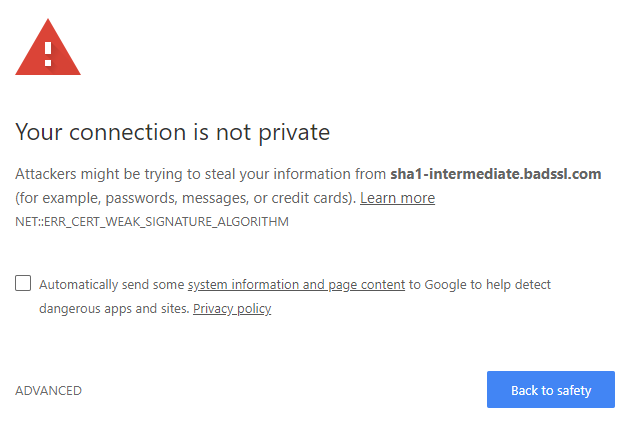 www.rapidsslonline.com
www.rapidsslonline.com
cert err signature weak invalid algorithm authority error fix google ssl chrome resources what outdated hashing certificate website
Secure Hash Algorithm (SHA-1) | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
sha algorithm hash
What Is Hash Function? And How Does It Work | Ssla.co.uk
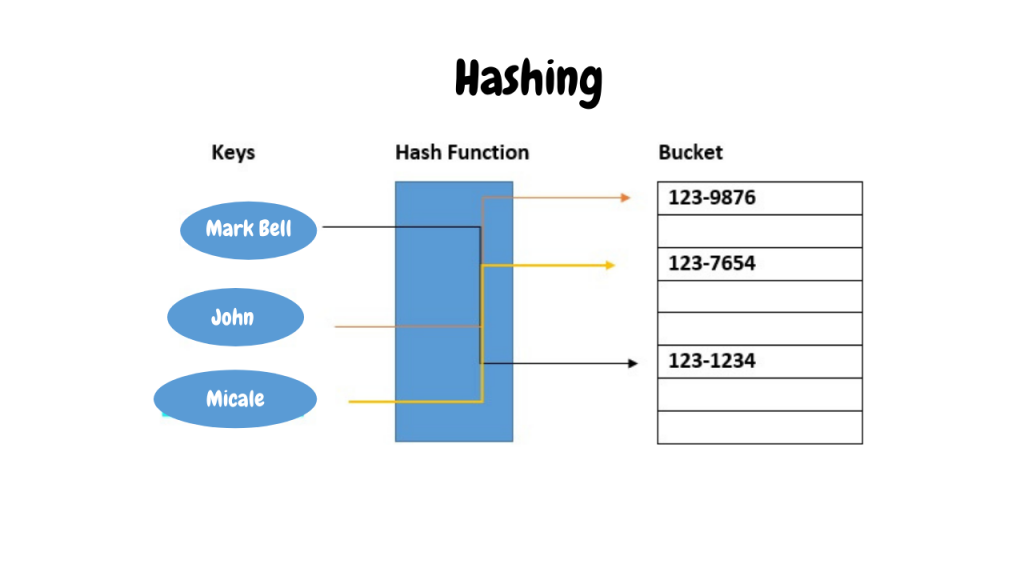 www.ssla.co.uk
www.ssla.co.uk
ssla
MD5 ALGORITHM.pptx
 www.slideshare.net
www.slideshare.net
Hash Functions: Definition, Usage, And Examples - IONOS CA
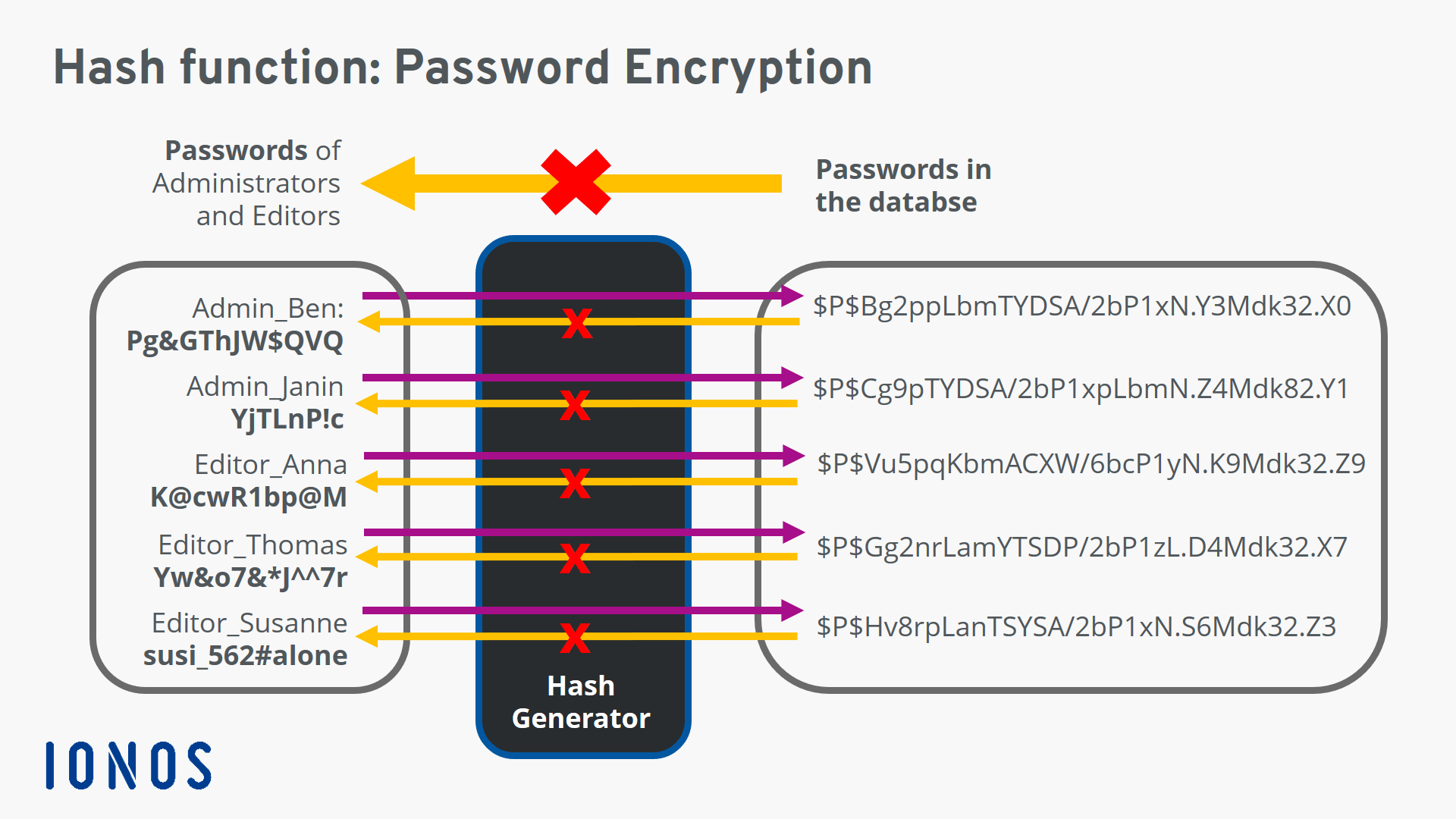 www.ionos.ca
www.ionos.ca
hash function example functions examples what passwords length definition strings fixed into ionos output database converted security server actual digitalguide
What Does Hash Mean In Python - What Does Mean
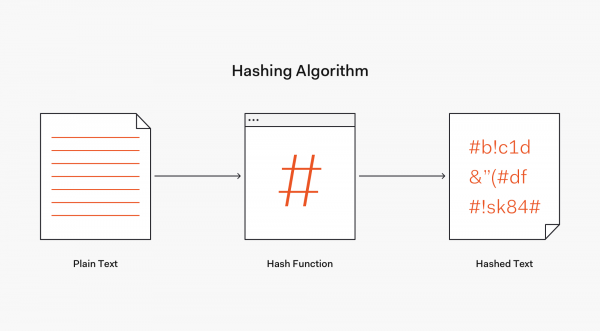 whatdoesme.blogspot.com
whatdoesme.blogspot.com
hashing auth0 signing significance client encryption hashed algorithms golang backend js python cryptographic créditos
Openvpn You Are Using Insecure Hash Algorithm
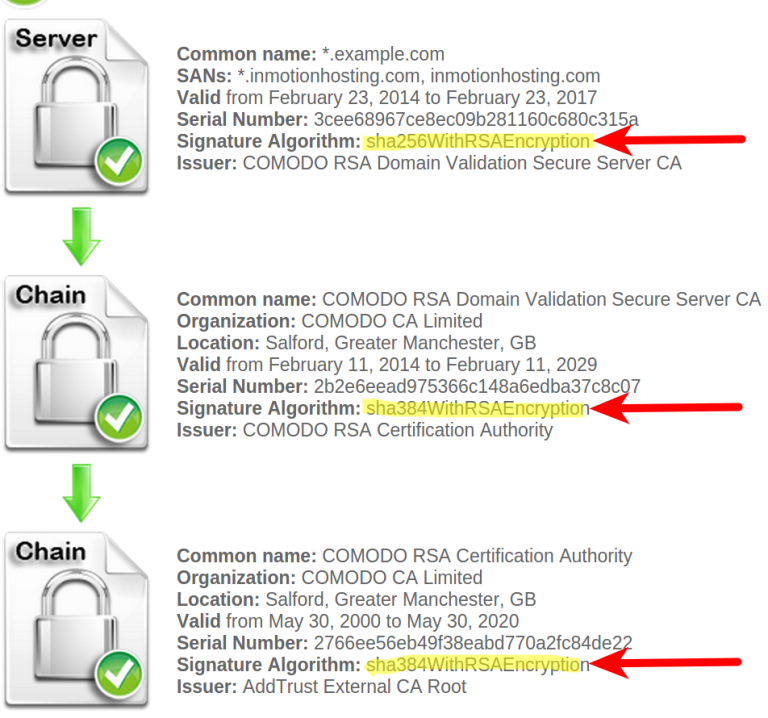 studyzonepiebarrelfuls.z21.web.core.windows.net
studyzonepiebarrelfuls.z21.web.core.windows.net
Error: Insecure Signature Digest Detected - SparkLabs
insecure digest detected error sparklabs
SOLVED: Question Sub-Question CLO Total Marks 1 - 2,3,5,7 10 2 2,3,5,7
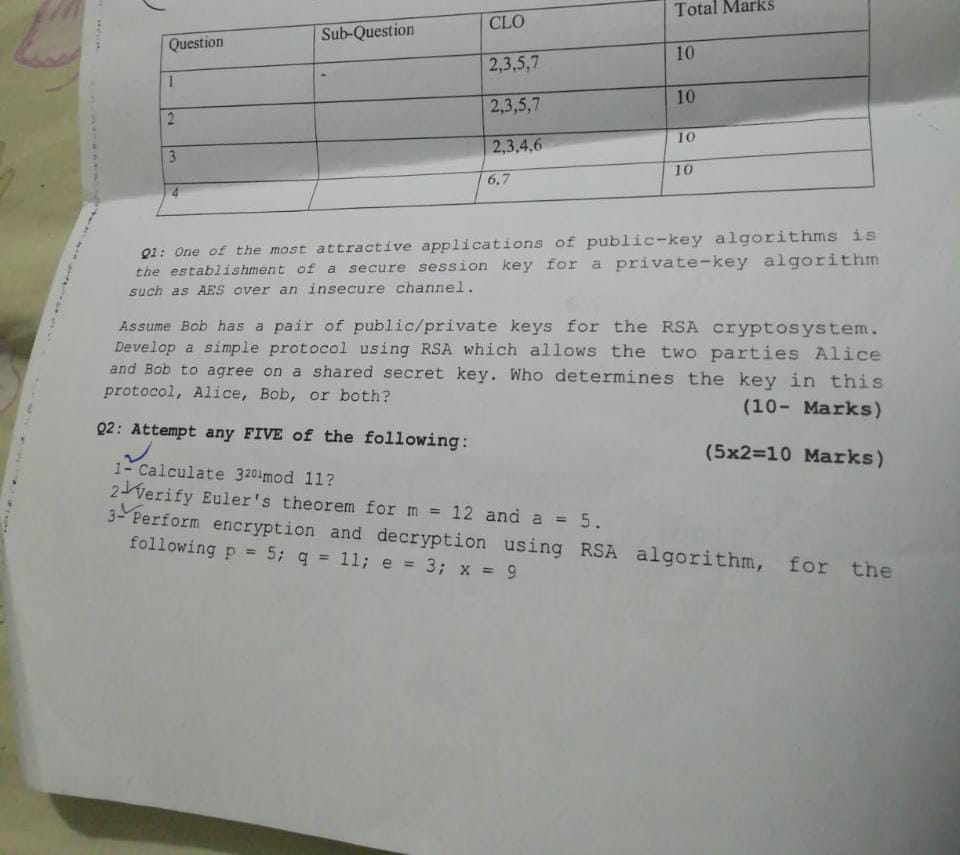 www.numerade.com
www.numerade.com
What Is Secure Hashing Algorithm (SHA) | SHA1 Vs SHA2
 www.https.in
www.https.in
Digital Signature Cryptography | Know 2 Major Forms Of Encryption
 www.educba.com
www.educba.com
signature digital cryptography security network software authentication development tutorials tutorial
MD5 Hash Algorithm: Understanding Its Role In Cryptography
md5 algorithm digest indexes integrated bolster frameworks
Hash Functions And Cryptography - Web3 Encyclopedia
 web3-encyclopedia.gitbook.io
web3-encyclopedia.gitbook.io
Php - Connections Using Insecure Transport Are Prohibited While
 stackoverflow.com
stackoverflow.com
Digital Signature
 mayurpahwa.com
mayurpahwa.com
Hamburger Hashbrown Casserole Is An Easy Ground Beef Dinner Recipe
 www.pinterest.ca
www.pinterest.ca
AES-256 Bit Encryption Algorithm Explained - Anonymistic
 www.anonymistic.com
www.anonymistic.com
certificates pki encryption certificate aes demystified algorithm cryptography
FILESHADER: ENTRUSTED DATA INTEGRATION USING HASH SERVER | PDF
 www.slideshare.net
www.slideshare.net
RT-AC87U & OpenVPN: Using Insecure Hash Algorithm In CA Sig | SNBForums
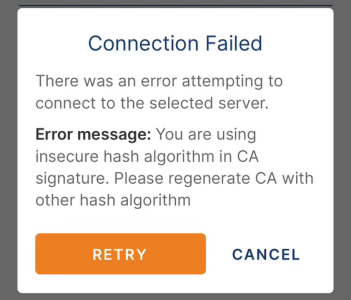 www.snbforums.com
www.snbforums.com
R8500 OpenVPN Error You Are Using Insecure Hash Al... - NETGEAR Communities
 community.netgear.com
community.netgear.com
Hash Function.pdf | Free Download
 www.slideshare.net
www.slideshare.net
What Is A Hash Function In Cryptography? A Beginner’s Guide - Hashed
 www.thesslstore.com
www.thesslstore.com
hashing cryptography algorithm digest illustration input hashed generates hexadecimal thesslstore
Digital Signature Algorithm (DSA) In Cryptography
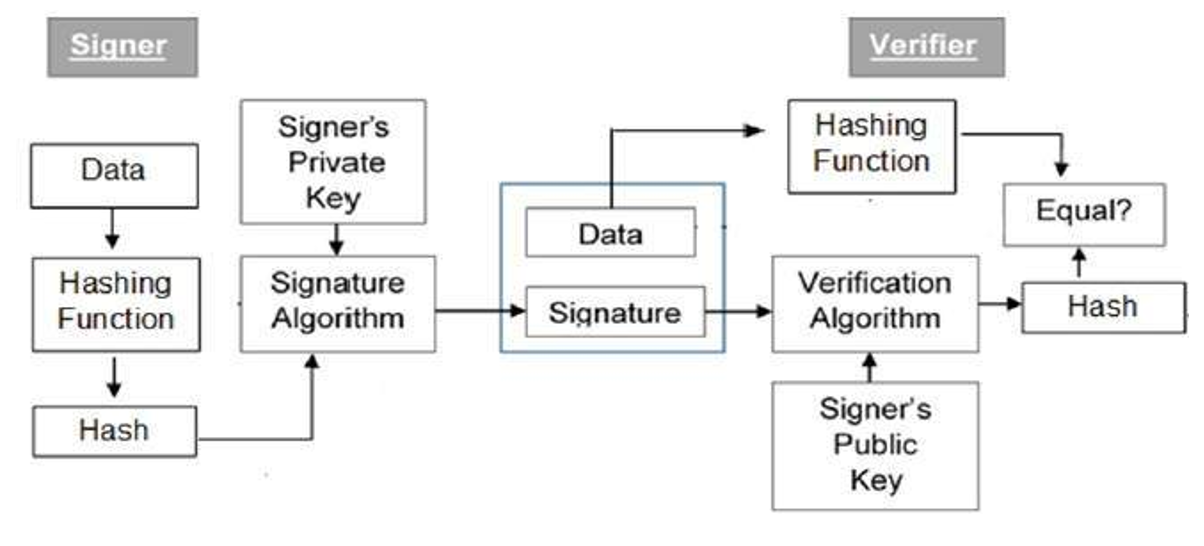 www.includehelp.com
www.includehelp.com
dsa cryptography signature algorithm
Insecure Design | Tutorials & Examples | Snyk Learn
 learn-web.snyk-internal.net
learn-web.snyk-internal.net
Insecure Has Algorithm In CA Signature : R/OpenVPN
 www.reddit.com
www.reddit.com
Hash functions and cryptography. Aes-256 bit encryption algorithm explained. Rt-ac87u & openvpn: using insecure hash algorithm in ca sig